Mini Key Log
 Mini Key Log is a light version of the world's most powerful surveillance software - PC Agent. Some features are not available in Mini Key Log. Mini Key Log is specially designed to monitor a computer quickly and easily. To get to know Mini Key Log better we offer a free trial version for download.
Mini Key Log is a light version of the world's most powerful surveillance software - PC Agent. Some features are not available in Mini Key Log. Mini Key Log is specially designed to monitor a computer quickly and easily. To get to know Mini Key Log better we offer a free trial version for download.
Recording features
Keyboard input

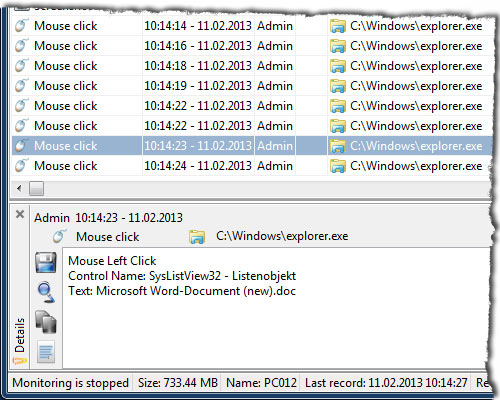
The keylogger function records keystrokes (including passwords), shortcuts, hotkeys as well as characters typed by using the Input Method Editor (IME).
Screenshots
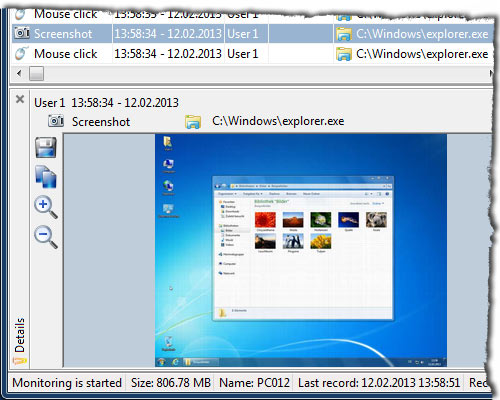
Captures screenshots of the windows, moved in the foreground and then in a specified interval. The motion detection as well as adjustable values for the dimension and quality can reduce the size of the screenshots drastically.
File operations
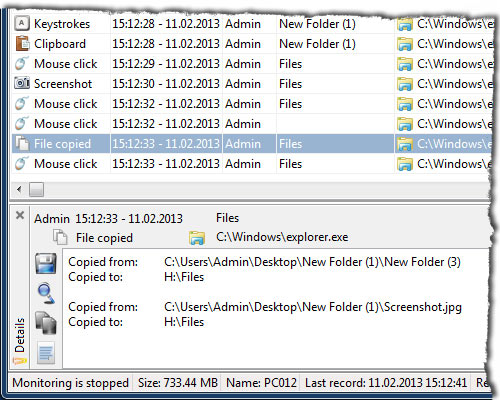
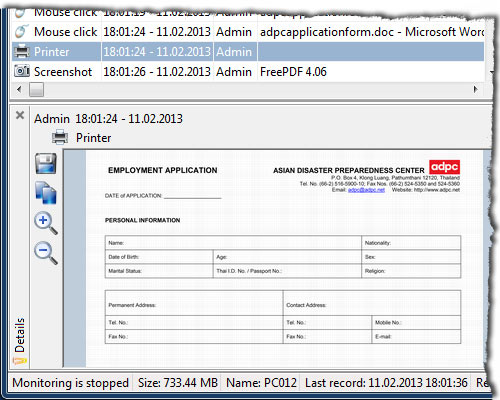
Records the names of files or folders, opened, deleted, renamed, copied or moved by the user.
Webcam

Captures pictures from a webcam in an adjustable interval. The motion detection as well as adjustable values for the dimension and quality can reduce the size of the pictures drastically.
Microphone
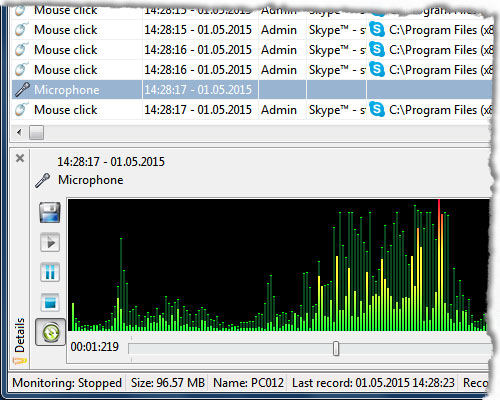
Records the noises from a connected microphone. The noise detection and an adjustable value for the quality can reduce the size of the records drastically.
Browsing History

Captures the URL of the visited website. All common browsers are supported. Such as: Google Chrome, Firefox, Opera, Internet Explorer, Microsoft Edge and many more.
More features
Invisible in the process list
Hides the monitoring process in the Windows Task-Manager or other process lists.
Selective user monitoring
Excludes users from the monitoring or records only certain users.
Automatic uninstall
Uninstalls the monitoring process automatically as soon as the monitoring starts on or after the specified date.
Delete records automatically
Deletes records automatically to avoid additional effort to delete the records manually.
Protection against unauthorized use
Protects the control center with a password against unauthorized use. This feature is only available with a valid license key.
Filter records
Records can be filtered according to many criteria. The process is very quick and easy to use. Usually only one click is required. Read more...